Remote access is a growing trend for businesses. It’s a tool used to allow a more flexible work culture, enabling employees to stay productive at work 27/7. As much as it can be helpful at times, remote access can cause a security havoc in your system as well. The sad reality with this technology is that it’s slowly becoming a target prey for modern hackers and online perpetrators. In this guide, will show you some of the security risks of using remote access technology.
What is Remote Access?
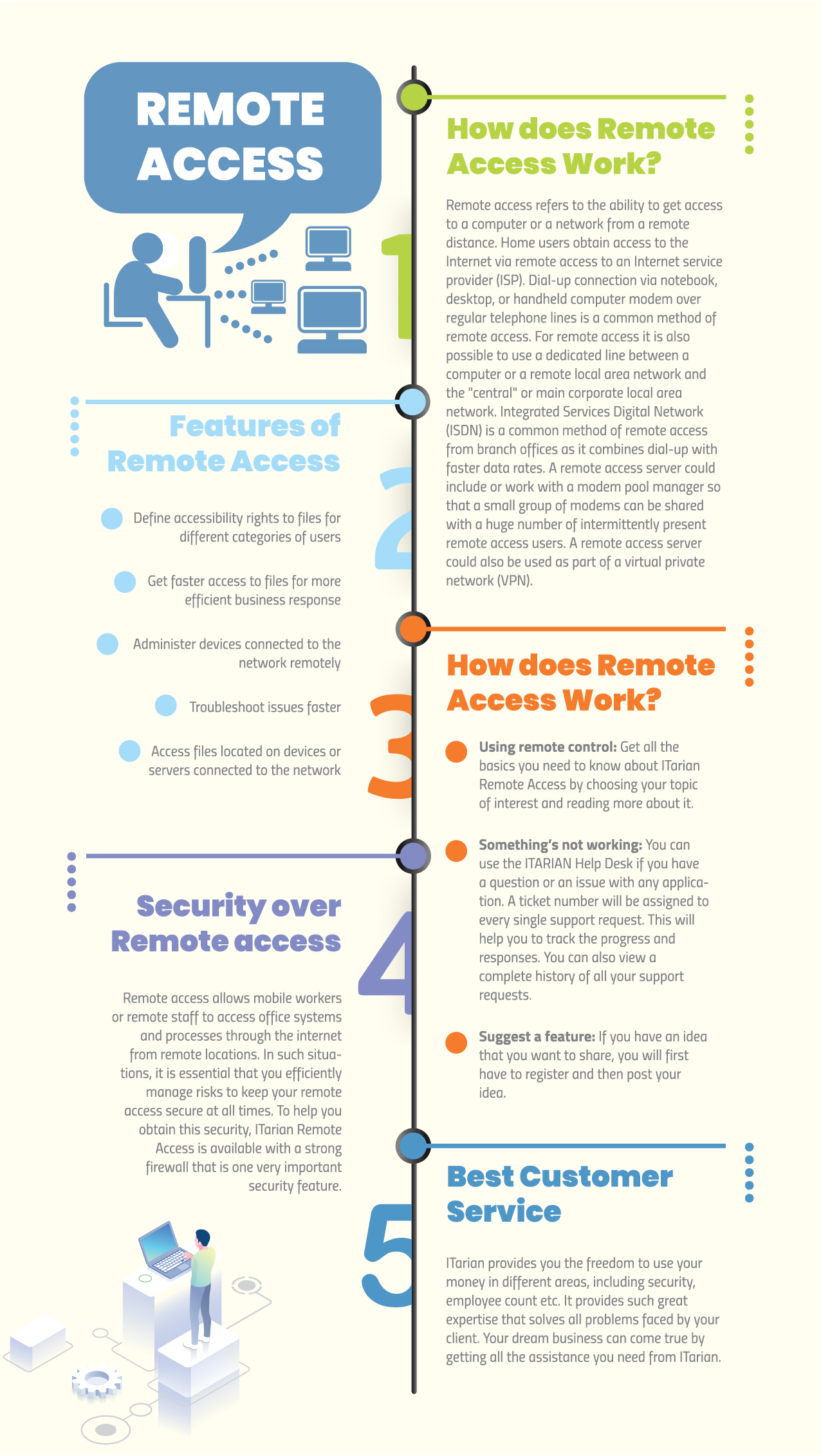
Remote access is a technology that allows users to access another computer remotely. Via a remote connection, the user can remotely connect to an endpoint machine as if he was sitting right in front of it. From there, he can perform several computing tasks a local user can. He can access files, use apps, troubleshoot technical issues, and even control the remote computer on his own.
Businesses that use remote access find that it helps with the overall productivity of their employees. With the help of this technology, it’s possible for them to work on specific business requirements even outside of a central work location. Those who are traveling, on leave, or simply can’t be at their office can still accomplish their daily work routines using remote access. Undoubtedly, this technology can be a great business ally especially in an era where the dynamics of business are moving at a faster rate.
IT professionals who serve a myriad of people across the globe can use remote access for their own benefit. Instead of providing the traditional on-site visit to clients, IT help pros can simply work on their clients technical issues without leaving their physical office desks. This allows them to save on time, money, and effort, and eliminate the need to travel from places to places.
The Dangers of Using Remote Access
Beyond its benefits and advantages, remote access can sadly, bring some level of security concerns to your business. If not implemented correctly, it can lead into a potential security incident where certain confidential files and information can be exposed and acquired. Here are the risks of using remote access:
1. Endpoint Devices – Companies that allow employees to work from home can be subjecting their networks to unwanted and malicious attacks. Employees who use their personal devices to connect to a corporate network can exploit their company’s own security system. The thing with this kind of practice is that your employees endpoint devices have their fair share of security flaws and complications. Some of them may be infected with malware and other viruses that can harm your own network’s security.
If these devices can connect to your network remotely, your corporate network is more likely to get infected by the same threats, too. That’s why it is important for businesses to require their employees to get their devices checked regularly. As much as possible, require them to install anti-malware software that can protect their devices from such malicious threats. In that way, your employees can safely connect to your network from anywhere at any time.
2. Poor Login Credentials – Most businesses nowadays only settle with simple ID numbers and passcodes. Having poor login credentials can be the first step to exploiting the vulnerabilities of your private system. Some companies even use easy and decodable passwords that don’t add up to their system’s security and protection. It’s just a sad reality that a simple passcode can be the cause of a major security incident to your own private corporate network.
What businesses can do is to use two-factor authentication to really strengthen their own remote access credentials. By implementing one, hackers will have a hard time breaking into your system as two identification codes are needed to successfully access your network. You can also create unique passwords to really ensure that your remote access codes aren’t hackable and decodable.
3. Poor Policies and Protocols – Remote access can only be harmful when certain policies and protocols aren’t implemented effectively. It is important for companies to know that remote access should only be used when needed. As much as possible, only those who need to use it must be allowed to connect to your corporate network outside of your central work location. Even for system administrators, all access must be disabled temporarily if the said technology isn’t being used to monitor and assess a bunch of office endpoint machines.
Remote access policies should also be reviewed regularly. Assign a specific team of security experts to come up with a list of protocols that will be implemented right away. See to it that this list of policies will be reviewed regularly to check for certain opportunities and loopholes. This way, your policies and protocols are strong enough to secure your company’s remote access technology.

Related Resources: